
|
IN BRIEF
|
In today’s digital age, it is crucial to remain vigilant against unusual requests for personal information. Scammers continuously devise new tactics to deceive individuals into divulging sensitive data. Awareness of the warning signs can empower you to identify these threats before they cause harm. Recognizing unfamiliar communications, spotting urgent pleas for information, and understanding common phishing tactics are essential skills for protecting oneself against online fraud. Being informed about what constitutes a suspicious request is the first step towards safeguarding your personal information.
In today’s digital landscape, identifying unusual requests for personal information is crucial to safeguarding your personal data. Scammers frequently employ various tactics to deceive individuals into divulging sensitive details, which can lead to identity theft or financial loss. This article delves into effective strategies for recognizing these requests while evaluating the advantages and disadvantages associated with them.
Advantages
One significant advantage of knowing how to spot unusual requests is the increased security it provides. By being aware of common tactics used by fraudsters, such as unsolicited phone calls or emails asking for sensitive information, individuals can better protect themselves and reduce the risk of falling victim to scams. Recognizing requests that demand immediate action often allows users to take a step back and assess the legitimacy of the request.
Additionally, understanding these requests helps build awareness about cybersecurity threats in general. Knowledge about how and why scammers operate empowers individuals to share information with friends and family, fostering a community that is informed and vigilant against phishing attempts and other malicious activities. Resources like the FTC can provide further insights into how to avoid common pitfalls.
Disadvantages
Despite the benefits, there are disadvantages to the heightened scrutiny that comes with spotting unusual requests for personal information. One of these includes the potential for paranoia or hyper-vigilance, which may lead individuals to second-guess legitimate requests. This skepticism can cause unnecessary disruption in essential interactions, such as during business transactions or legitimate account verifications.
Furthermore, being overly cautious can lead to missed opportunities, especially in situations where quick responses are necessary, such as job offers or important financial notifications. As technology evolves, scammers continually adapt their techniques, making it challenging to discern genuine outreach from scams. Therefore, while caution is important, it is equally vital to balance vigilance with trust in secure channels.
Key Takeaways
Identifying unusual requests for personal information is essential in protecting oneself from fraud. While the advantages of increased security and community awareness are significant, it is equally important to be mindful of the drawbacks of paranoia and missed opportunities. By staying informed and utilizing resources available online, individuals can better navigate the complexities associated with online scams.
Scammers increasingly employ sophisticated methods to deceive individuals into sharing sensitive data. Recognizing the signs of these unusual requests can be vital in protecting personal information. This guide outlines key indicators to help identify potential scams and offers practical tips for safeguarding your data.
Understanding the Request
When you receive a request for personal information, it’s essential to assess the context. Questions to consider include: Who is asking for information? Why do they need it? A legitimate organization will provide clear reasons for their request and often allow you to verify their identity.
Red Flags to Watch For
Be on alert for red flags that may indicate a scam. Common signs include unsolicited messages asking for sensitive information, urgent requests for money, or vague explanations regarding the necessity of your details. Pay attention if the communication lacks personalization, as it may suggest a generic phishing attempt.
How to Verify the Source
Before sharing any personal information, verify the source of the request. You can contact the organization directly using official contact details found on their website. Do not use contact information provided in the suspicious message. This step ensures you’re communicating with the legitimate party.
Avoiding Compromised Communication Channels
Exercise caution with unsolicited phone calls, texts, or emails. If a contact claims to be from a recognized company but uses a non-official email or phone number, it’s best to remain skeptical. Reputable organizations typically do not ask for sensitive information through these channels.
Investigating Suspicious Activity
If you suspect you may have encountered a scam, investigate further. Monitor your accounts for any unusual activities. For example, if your Google Account prompts unusual activity notifications, it may indicate someone else is using it.
Recognizing Phishing Attempts
Beware of vague greetings or messages that invoke a sense of urgency. Phishing emails often contain generic salutations and may threaten account suspension due to a billing problem. Always scrutinize such messages critically.
What to Do If You Suspect a Scam
If you find yourself in a situation where you suspect a request for personal information is fraudulent, do not engage with the sender. Report the incident to relevant authorities and consider seeking guidance on recovery of your personal information, especially through established resources like online-scams.com.
Taking these precautions seriously can help you protect yourself from becoming a victim of online scams and keep your sensitive data safe.
Identifying unusual requests for personal information is essential in protecting yourself from scams and phishing attempts. Unsolicited messages that urge you to provide sensitive data can lead to identity theft and financial loss. This guide provides actionable tips to help you recognize and respond appropriately to these suspicious inquiries.
Recognizing Unsolicited Messages
One of the first steps in spotting unusual requests is being aware of unsolicited messages. These can come in various forms such as emails, texts, or phone calls from unknown sources. Always be cautious when receiving messages from unfamiliar senders or those that seem out of the ordinary. According to the Virginia529 blog, common red flags include a sense of urgency or threatening language. If someone pressures you to act quickly, take a step back and evaluate their request.
Questioning Request Legitimacy
When faced with a request for personal information, it’s crucial to ask a lot of questions. Seek clarity by verifying the identity of the requester. Legitimate organizations will not hesitate to provide verifiable information. If the request seems vague or if the person refuses to provide their credentials, this can indicate a scam. Furthermore, avoid clicking on links or downloading attachments from unknown senders as these could contain harmful malware.
Checking for Poor Grammar and Spelling
Another important aspect to consider is the quality of the language used in the communication. Scammers often use generic greetings, awkward phrasing, or grammatical errors in their messages. If you receive an email that contains these issues, it is likely a phishing attempt. Always approach such messages with skepticism and consider reporting them to authorities. More information on how to recognize and avoid phishing scams can be found on the FTC website.
Identifying Emotional Manipulation
Be cautious of requests that invoke strong emotions. Scammers often create a sense of panic by claiming that your account has been compromised or that there is a serious issue that requires immediate action. Always take a moment to verify such claims through official communication channels rather than reacting impulsively based on fear. This strategy can help you avoid falling victim to scams.
Reporting Suspicious Communications
If you suspect that a request for personal information is fraudulent, reporting it can help protect yourself and others. You can take action by visiting resources that outline how to spot and report scams, such as the Texas Attorney General’s website. They provide useful guidance on what steps to take once you encounter a suspicious communication.
Understanding Scamming Techniques
Finally, educating yourself about various scamming techniques can empower you to spot unusual requests with greater accuracy. Recognizing the signs associated with different types of scams, such as tech support scams and subscription scams, can significantly reduce your risk of falling prey to these schemes. For more information on how these scams operate, check out Online Scams.
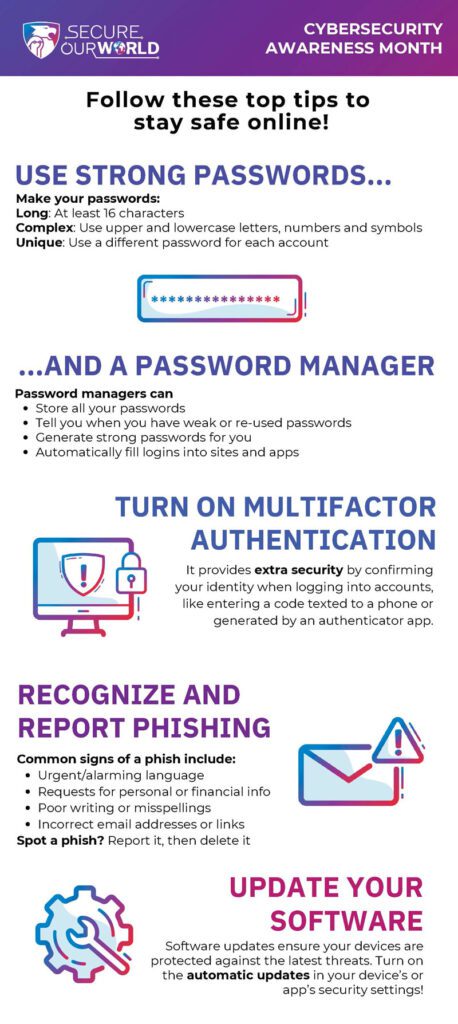
How to Spot Unusual Requests for Personal Information
| Indicators | Response |
| Unsolicited messages | Ignore and do not respond |
| Sense of urgency | Take a moment to verify the source |
| Generic greetings | Be cautious; reputable entities use your name |
| Request for sensitive data | Never provide personal information |
| Poor grammar or spelling | Treat it as suspicious |
| Unknown sender | Verify their identity before engaging |
| Suspicious links or attachments | Do not click or download anything |
How to Spot Unusual Requests for Personal Information
Scams and phishing attempts often come disguised as legitimate requests for personal information. It’s essential to stay vigilant and recognize when something doesn’t seem right. Unexpected messages from unknown contacts asking for sensitive data should raise immediate red flags. Always question the authenticity of these messages.
One common tactic used by scammers is to create a sense of urgency. When approached with alarming claims, such as your account being compromised or needing to confirm details urgently, take a step back. Legitimate companies typically do not pressure you to act quickly. Instead, they allow you to verify the request through official channels.
Another warning sign is poor grammar or spelling in the correspondence. Many phishing attempts come from non-native speakers and contain unusual syntax. Be cautious of messages that appear unprofessional, as they often signal a scam.
If you receive a request for financial information or money, consider it suspicious. Legitimate organizations will not ask you to send funds through unsecured channels or share your bank details via text or email. Always verify claims by contacting the organization directly using official contact details.
Pay attention to the sender’s email address or phone number. Phishing attempts may come from slightly altered versions of legitimate addresses. Always check for discrepancies and avoid engaging with unrecognized contacts.
In summary, being aware of the signs and exercising caution can help you protect your sensitive information. It’s always better to verify than to risk your personal data falling into the wrong hands.
How to Spot Unusual Requests for Personal Information
In today’s digital age, it is crucial to be vigilant about any requests for personal information. Scammers frequently attempt to harvest sensitive data through deceptive means. This article will outline the vital signs of unusual requests, enabling you to protect your personal and financial information effectively.
Recognizing Suspicious Communication
Unsolicited Contact
One of the first red flags of unusual requests is unsolicited contact. If you receive a message, email, or phone call from an unknown entity asking for personal information, proceed with caution. Legitimate organizations rarely ask for sensitive details through such channels. Always verify the source before proceeding.
Generic Greetings
Watch out for communication that uses a generic greeting. Messages that address you as “Dear Customer” or similar terms often indicate a potential scam. Genuine companies typically use your name and personal details to make the communication more trustworthy. If the sender lacks personalization, this could be a sign of phishing.
Excessive Urgency and Threatening Language
Pressure Tactics
Scammers often create a sense of urgency in their communications. Phrases like “Immediate Action Required” or “Your Account Will Be Suspended” are common tactics used to pressure individuals into providing sensitive information quickly. Take a step back and critically evaluate the situation; legitimate requests generally allow time for reflection.
Threats of Consequences
Threatening language is also a significant warning sign. If the requestor implies legal actions or consequences for failing to comply, it could be a scam. Always report such communications to the relevant authorities instead of responding. Trust your instincts when the tone feels unjustified.
Analyzing the Sender’s Information
Unfamiliar or Unusual Senders
Additionally, consider the sender’s email address or phone number. Look for discrepancies in the email address—especially if it contains a minor alteration, such as a misspelled domain name. Scammers utilize tactics like spoofing to make correspondence appear official while hiding their true identity.
Grammar and Spelling Errors
Pay attention to the language used in the communication. Spelling mistakes and poor grammar are common hallmarks of phishing attempts. If the message seems unprofessional or riddled with errors, it’s a significant indicator that the request is dubious.
Types of Information Requested
Requests for Personal Information
Be wary of requests that ask for personal information, such as Social Security numbers, bank details, or login credentials. Authentic entities will not request confidential information through insecure channels. If the request seems excessive or unnecessary, it’s a sure sign to question its legitimacy.
Payment Requests
Another common tactic is the request for payments using unconventional methods, such as gift cards or wire transfers. Legitimate businesses generally offer standard payment methods, such as credit cards or bank transactions. If you’re asked to pay using unusual methods, this should immediately raise a red flag.
Learning how to spot unusual requests for personal information is an essential skill in today’s digital landscape. By familiarizing yourself with these signs, you can guard against potential scams and maintain your security effectively.
How to Spot Unusual Requests for Personal Information
Recognizing unusual requests for personal information is crucial in today’s digital landscape, where scams and phishing attempts are rampant. One of the first signs to watch for is an unsolicited message from an unknown sender. Legitimate organizations typically do not ask for sensitive data through email or text messages. Always verify the identity of the requester before providing any personal details.
Another critical indicator is the use of urgency or threatening language. Scammers often create a sense of panic to rush you into making hasty decisions. If an email or message prompts you to act quickly to save an account or prevent a violation, take a step back. This is a common tactic used in phishing attempts.
Additionally, look for spelling and grammar errors. Many phishing emails originate from foreign sources and may contain awkward phrasing or misspellings. A legitimate representative from a reputable company is unlikely to send poorly written communications.
Moreover, any request for sensitive information such as your social security number, bank account details, or passwords should raise a red flag. Reputable organizations will have secure methods for you to provide such information, if required at all.
Lastly, be cautious of pop-up alerts or unexpected requests that appear while browsing the web. These could be attempts to lure you into providing personal data under false pretenses. Always prioritize your security by questioning the legitimacy of these requests and performing due diligence.
Frequently Asked Questions on Spotting Unusual Requests for Personal Information
How can I recognize unusual requests for personal information? Look for unsolicited messages that ask for sensitive data, particularly those that create a sense of urgency or threaten consequences if you do not respond.
What types of communication should I be wary of? Be cautious of unknown emails, texts, or phone calls that require any personal details or money.
What are some signs of a phishing attempt? Common indicators include generic greetings, requests for verification, and spelling or grammar errors in the communication.
What actions should I take if I receive a suspicious message? Do not respond or click on any links. Instead, verify the sender through official channels.
How important is it to ask questions when responding to unusual requests? Asking specific questions can help you gauge the legitimacy of the request and identify potential scams.
What should I do if I believe I’ve provided personal information to a scammer? Take immediate action to lock your accounts and monitor them for any suspicious activity.
Are there specific phrases that indicate a scam? Yes, phrases that create a sense of urgency or mention prizes, loans, or unsolicited help are often red flags.
